This was a 3 day rush investigation into a recent security issue. Hackers had obtained customer details from external sources and were then accessing accounts and placing fraudulent orders.
As a counter measure the business wanted to implement 2 factor authentication immediately and also enabled logic where any account changes wiped sensitive data from their accounts.

Below is an investigation into a number of questions we wanted to prove out before IT decided to steam ahead with a solution, a POC using an auth app to verify details was already being worked on.
- How was our system compromised
- How could it be better
- Is 2 factor or multi factor a valid option
- If it is whats the best way
- If not what is
The situation
- Wiggle customers have reported suspicious ordering activity on their accounts.
- It was determined that Wiggle had not been directly hacked but hackers had acquired customer login details externally.
- Hackers were then probing Wiggle to see what user details would work.
- Hackers were then logging into customers account and placing orders.
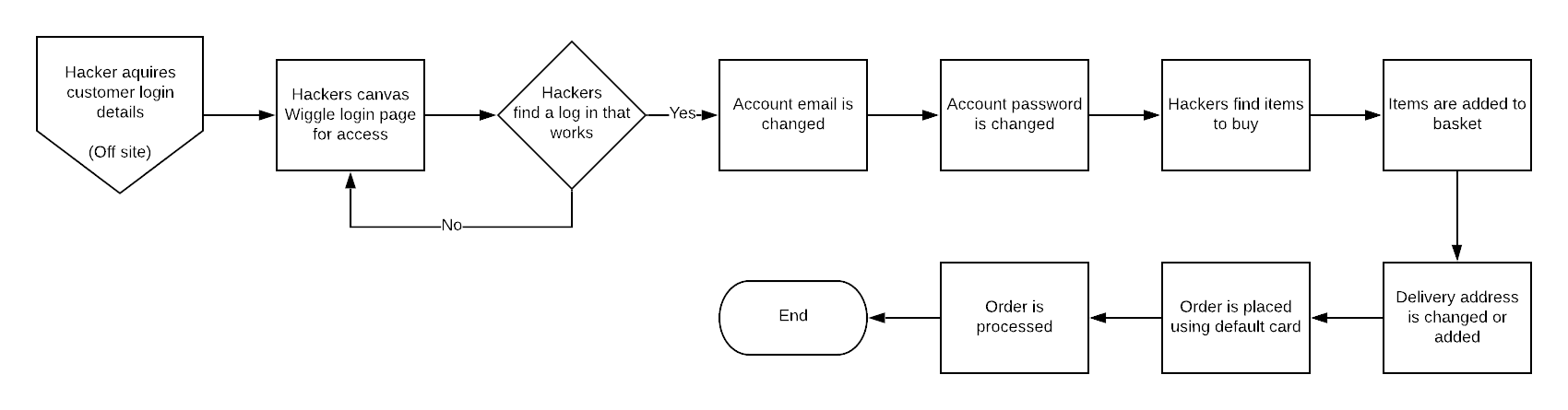
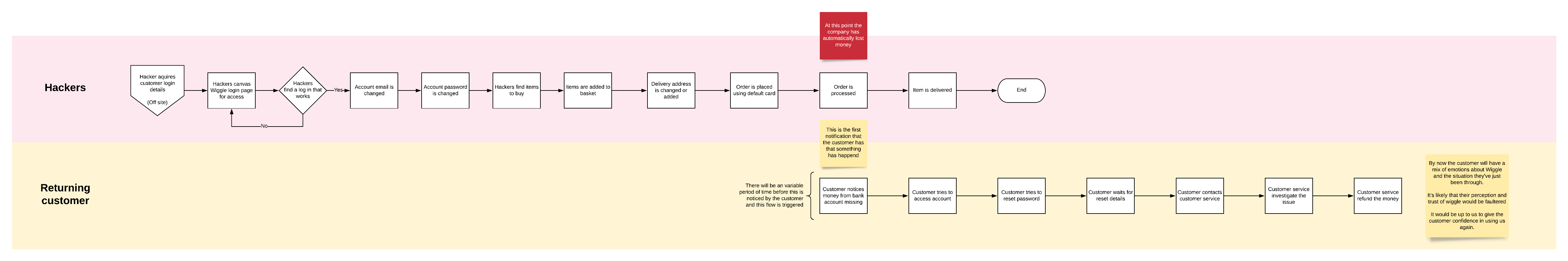
The issues in that vs flow
- Customers reuse the same password making it easy to canvas.
- There was no password strength check on sign up (Wouldn't of mattered in this case)
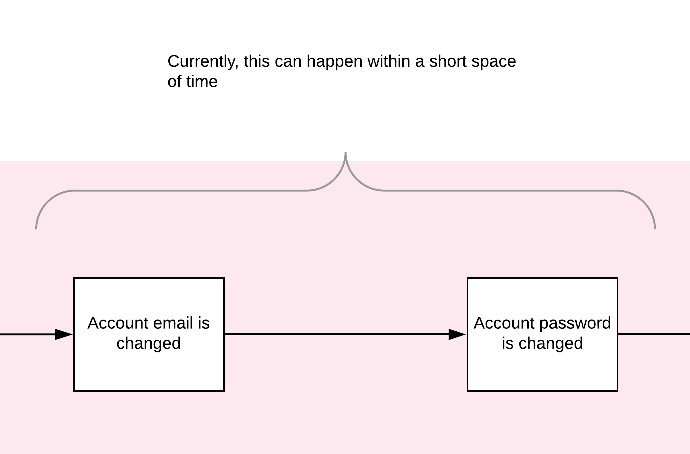
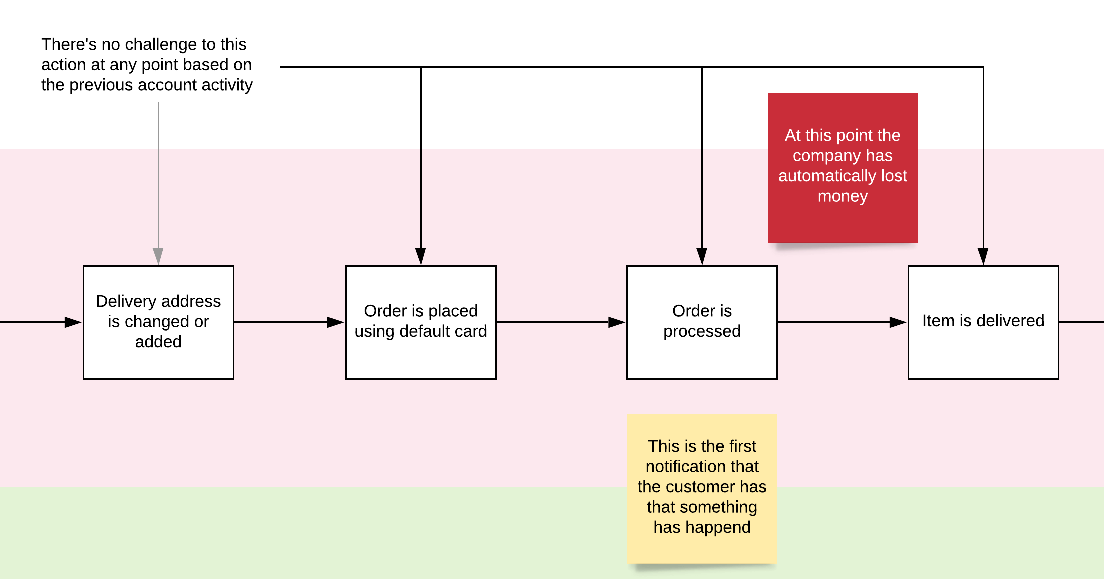
- All contact and access information was changed within minutes.
- All information was changed without challenge.
- The customer was not notified about the changes happening on the account
- No security preference check up ever
Analysis of current system
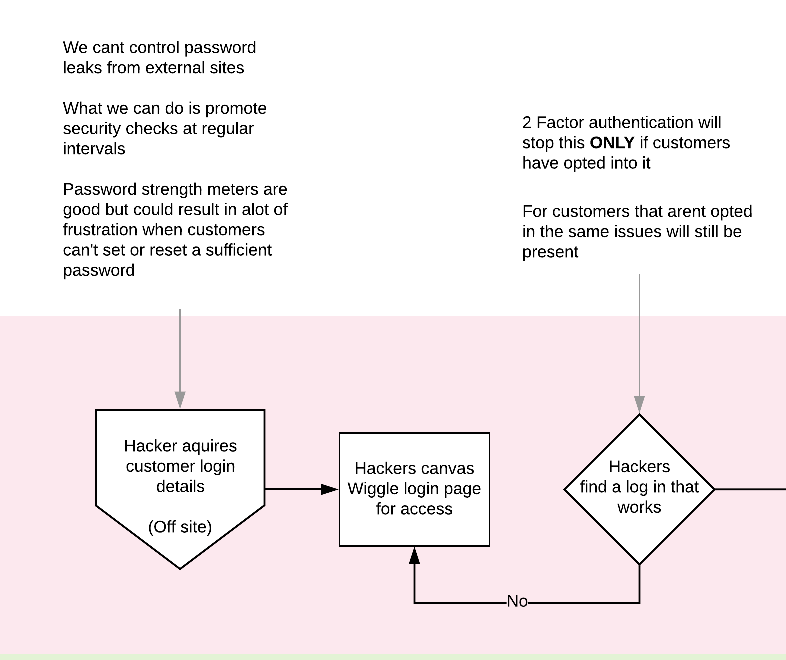
Two Factor authentication in retail is minimal with only some of the biggest names having introduced it into their systems (eBay, Apple, Amazon, Etsy, Best buy).
It is also not actively promoted on login or sign up and its benefits wouldn't be felt by everyone.
Regardless of customer opt in it doesn't effect the returning customer flow.
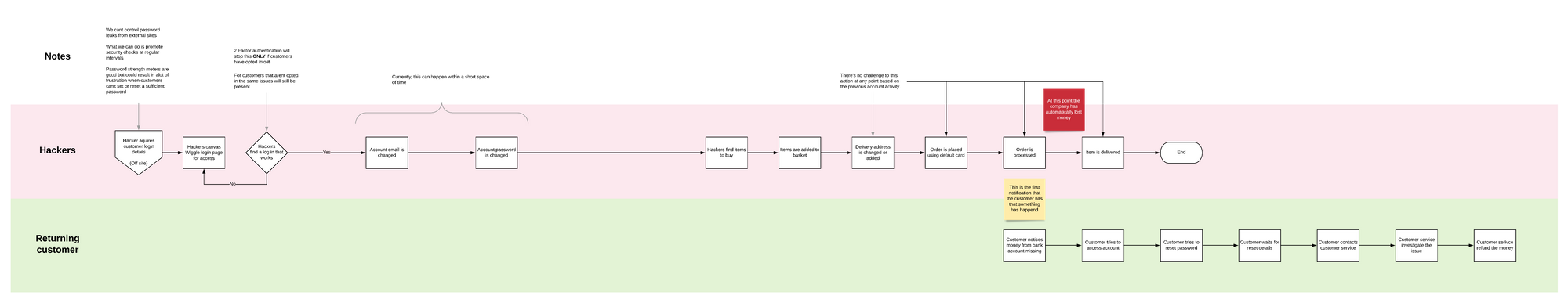
Is MFA right?
Below are result from an onsite poll that we put out to try and determine the potential uptake or appetite for MFA on Wiggle. I've also included a couple of sections from various articles about MFA, and security which I came across in my research.
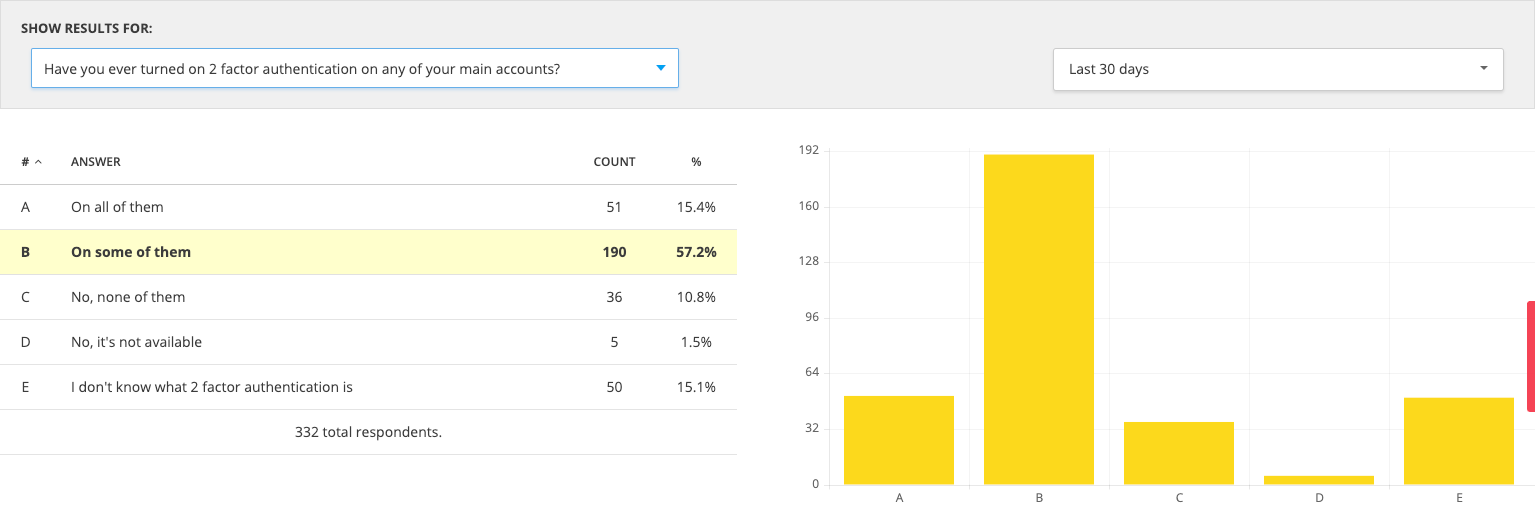
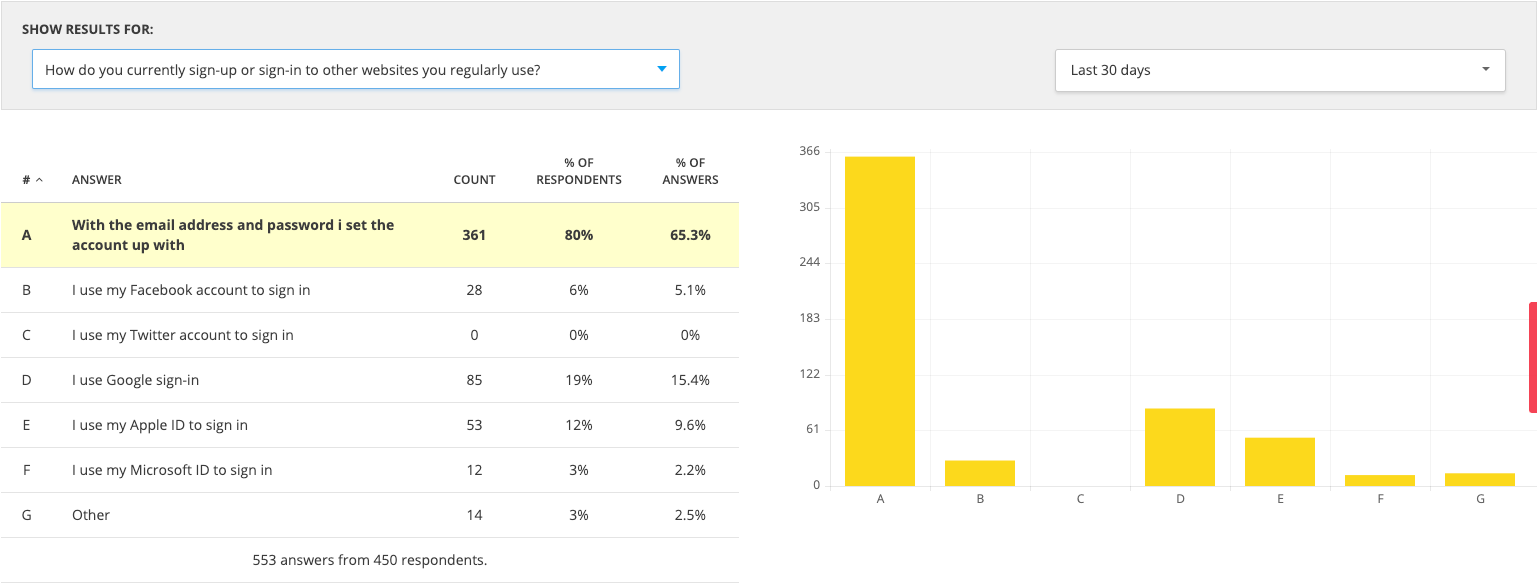
Results
- When asked how they currently sign up for accounts on websites they use regularly, 65% said they prefer to use and email and password as opposed to any kind of single sign on.
- When asked if they had 2 factor authentication on them 57% had it on some of their accounts
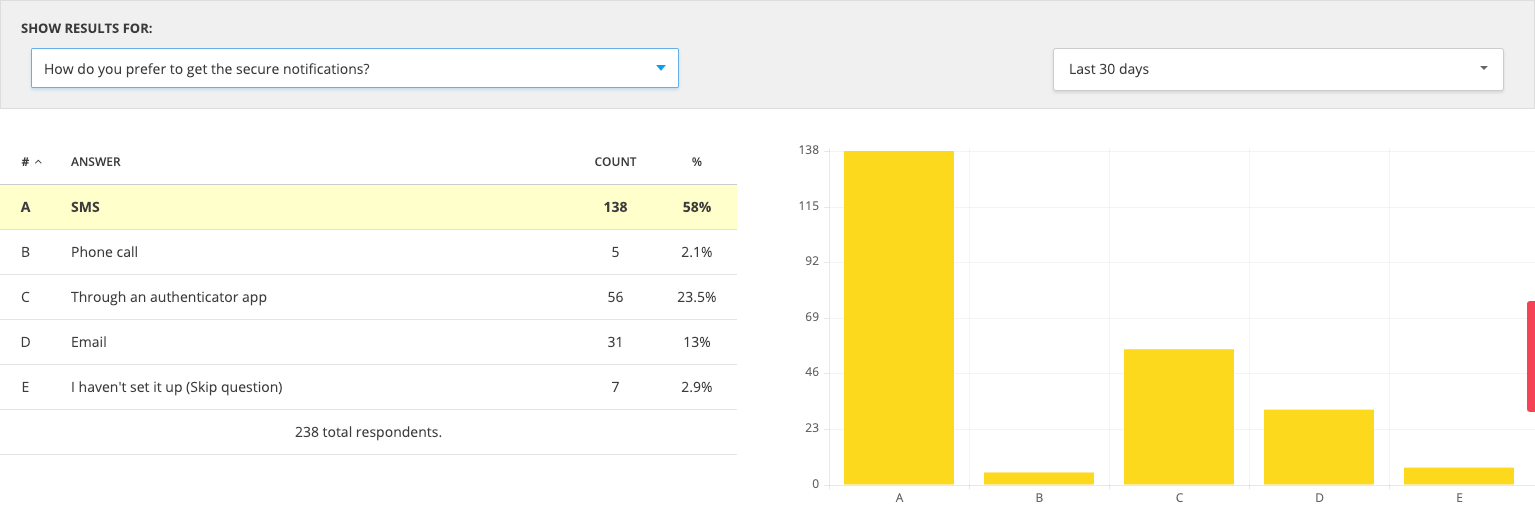
- SMS was the most popular notification type 58%
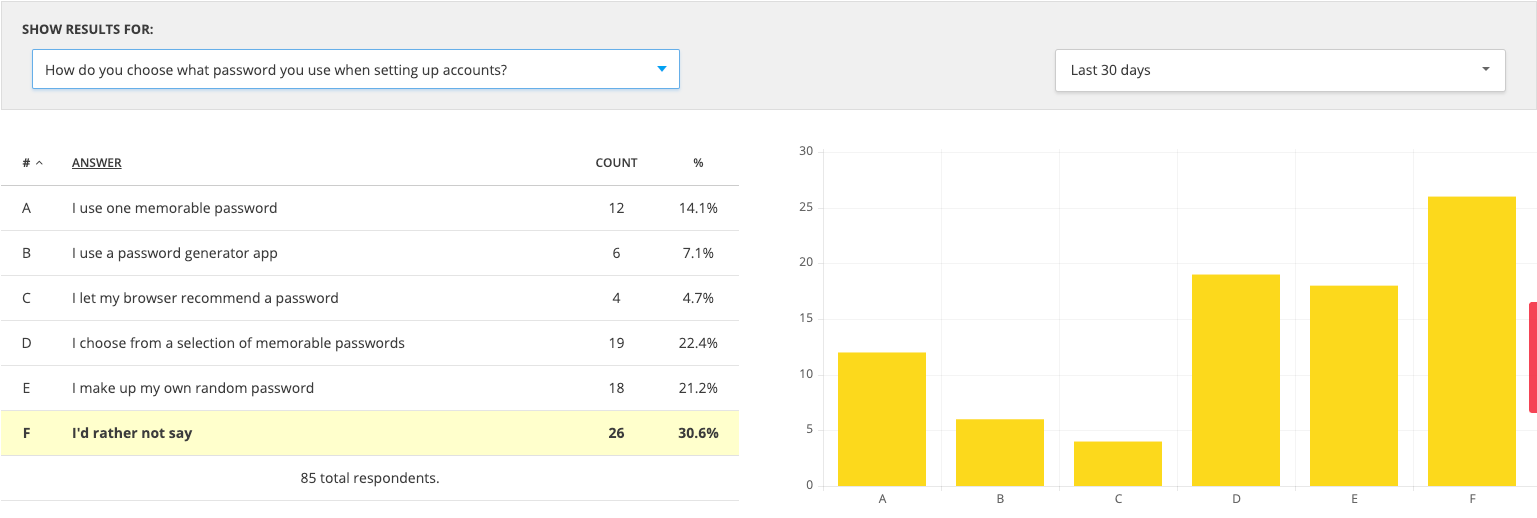
- And when asked how they choose their password 30.6% didn't want to answer that question but the larger portion choose from a selection of memorable passwords or they make up a random password.
- 14% reuse the same password

Popular auth types
SMS-based authentication remains the most popular 2FA factor at 72% usage, followed by email (57%), authenticator app (36%), and phone callback (30%). SMS was also the most popular answer when respondents were asked about their preferred authentication factor, indicating their familiarity with this option makes it more convenient and appealing.
Kelly Sheridan, Dark reading
Security & Human Factors
The big lies of computer security?
- Random passwords are more secure.
- A system-selected password is more secure than one the user chooses.
- Long passwords are more secure than short ones.
- Forcing the user to change passwords frequently increases security.
- Requiring different passwords for different systems increases security.
All of these statements would be true if we did not have to consider the human factor.
Jakob Nielsen, NN/g
The Human Factors of Password Security
Security experts often recommend that users select different passwords for each online service they belong to and that users change their password with regular intervals.
Good advice in theory, but in practice these experts have forgotten to consider the human factors of password security. Most security breaches happen because of various human weaknesses (e.g., users who give their password in response to email from a person claming to be a system administrator who needs the password to investigate a possible intruder!).
A simple human factors analysis shows that no normal human can remember 50 different random combinations of characters, leading to one of two common solutions: either users select non-random passwords that are easy to remember (and easy to crack), or the users write down the passwords on a piece of paper or in a file on their system (also a major compromise of security). Please note: people do this not because they are stupid or want to make their system easy to crack, but because it is physically impossible for them to do otherwise as long as they are required to have more than a very small number of passwords.
My solution is to get each user to select a very small number of truly random passwords, use the same passwords for many applications, and never write a password down. Admittedly, this is less secure than the hypothetical user who is able to memorize fifty different random passwords, but only a handful such people exist in the world.
Jakob Nielsen, NN/g
Multi Factor Authentication (MFA) Competitor research
I looked around for a number of retail MFA implementations to see how they had done it, what security precautions they had in place (that I could tell) and how they dealt in general with account security.
Turns out there's not a lot of online retailers with MFA on their systems, this kind of tech appears to the standard for business and banking but not retail.
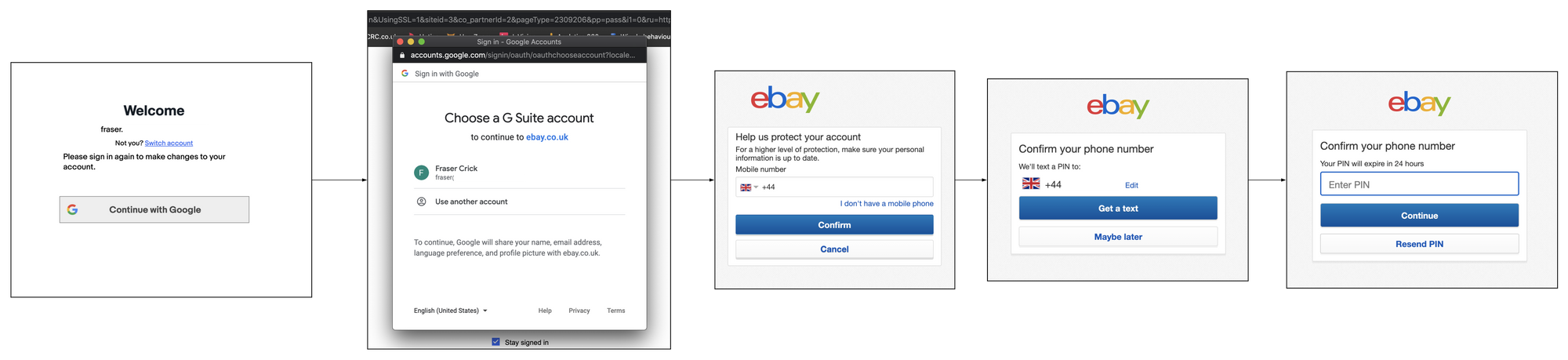
ebay
eBay's 2 factor enrolment is optional. Its activated through the account section under the password and security section but it doesn't look like customers are prompted to activate it anywhere in the journey.
Authentication is only triggered once per device or browser and It is not linked with any activity in checkout.
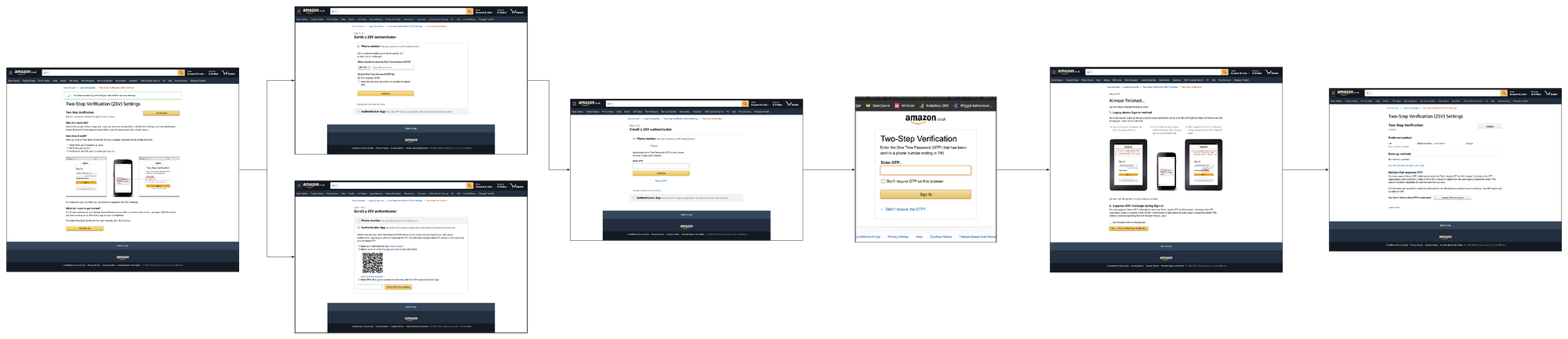
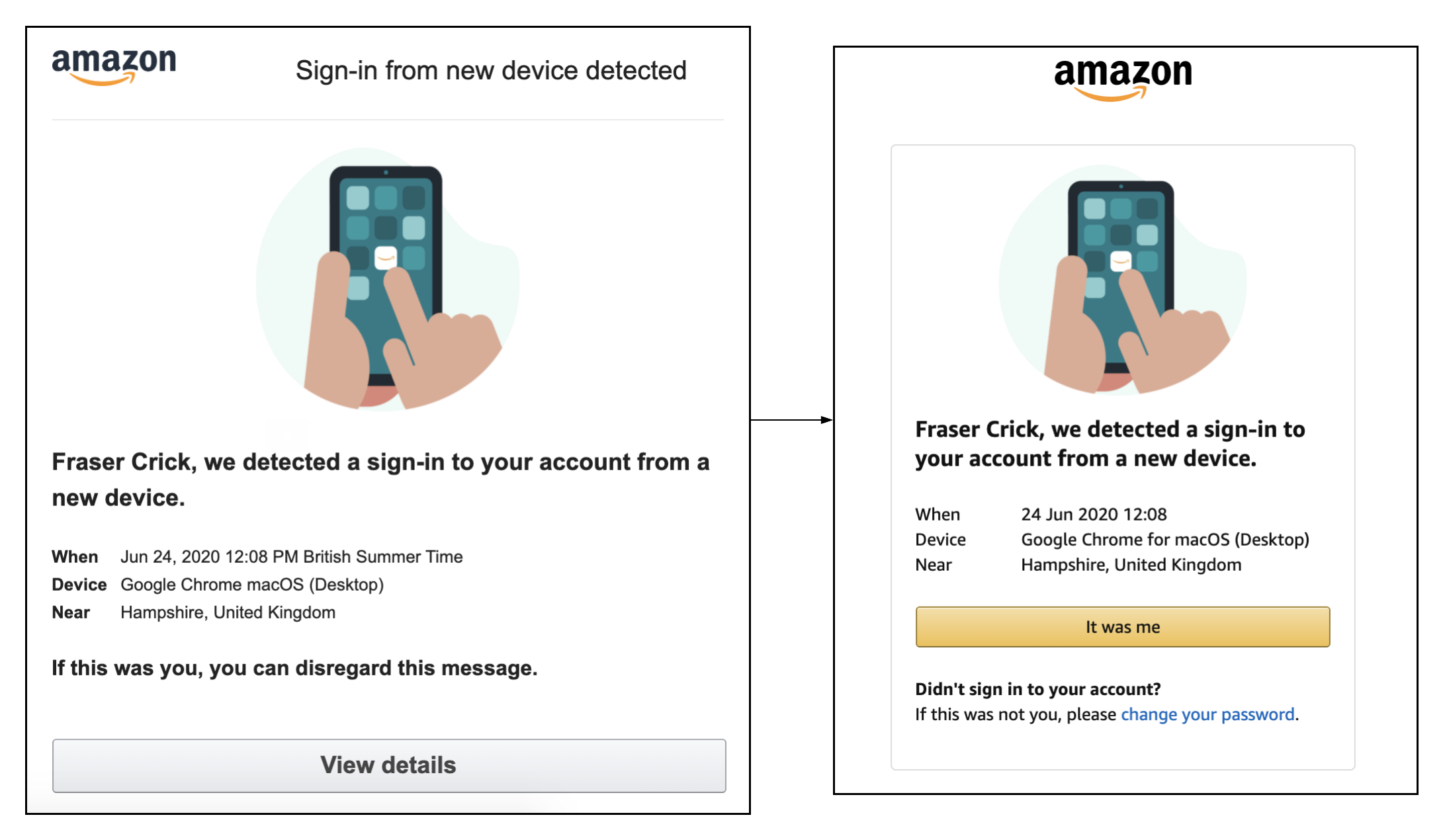
Amazon
Amazon's two factor authentication is optional. It is found under the password and security section of the account page.
The authentication is only triggered when a login happens on an unknown browser or device. If two factor is not enabled on an account the customer receives an email saying that there's been activity on the account and for them to accept or deny if it was them.
The authentication is not linked to any activity in the checkout and the journey is exactly the same with or without two factor authentication enabled.
Our suggestions
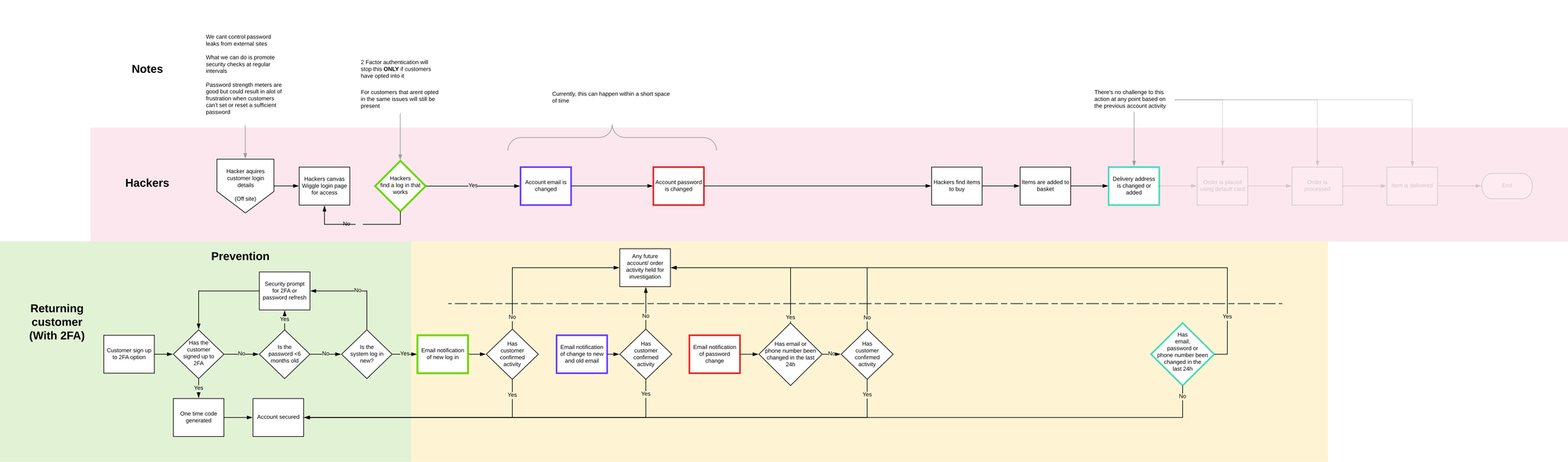
While this looks far more complicated than what we currently have it actually is a lot simpler. This idea gives the security of the account over to the customer and is more about fraud prevention than recovery.
Top and bottom flows are positioned to work parallel with each other, If something is happening on the top then theres a direct action at the bottom.
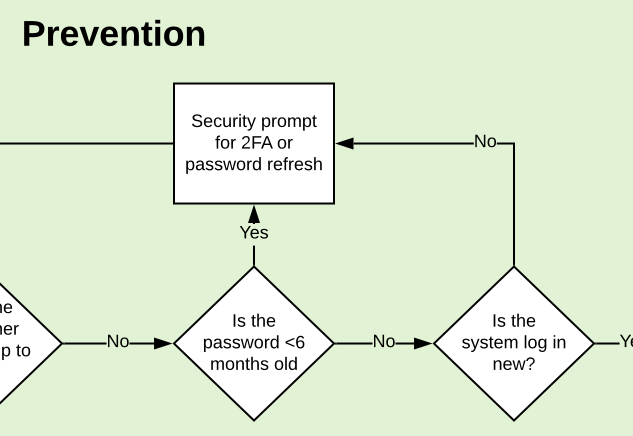
We've built 2 factor authentication but we've also got a security check up campaign as well. This would check how old the customer's password is and prompt the customer for a password refresh or to sign up to 2 factor auth.
This would be designed to address the human flaws in security and encourage customers to change their password or adopt 2 factor.
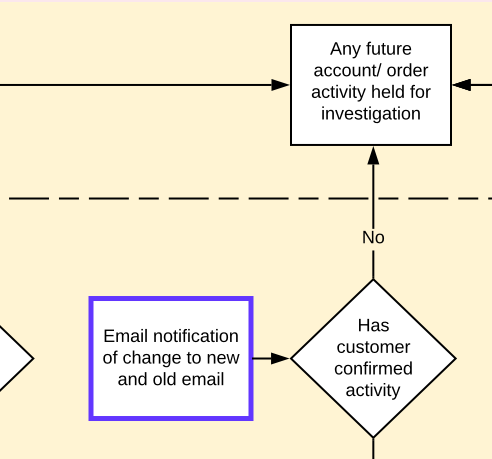
We now have two outcomes that account activity can be labeled as. Account secure or Account held.
You'll notice that all decisions lead to one or the other. This would be designed to allow the account to function normally should it need to and also block and stop any suspicious activity.
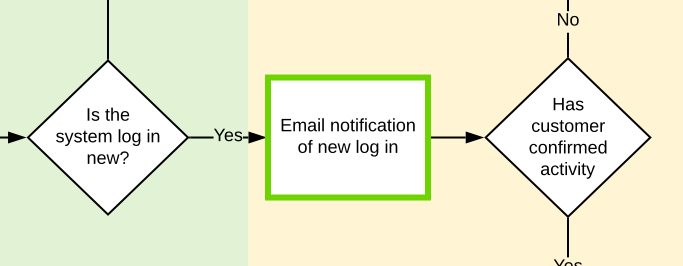
The customer contact point has been brought forward to right at beginning of the attack. The customer is now alerted that activity is happening on the account and needs to acknowledge it before anything else can happen
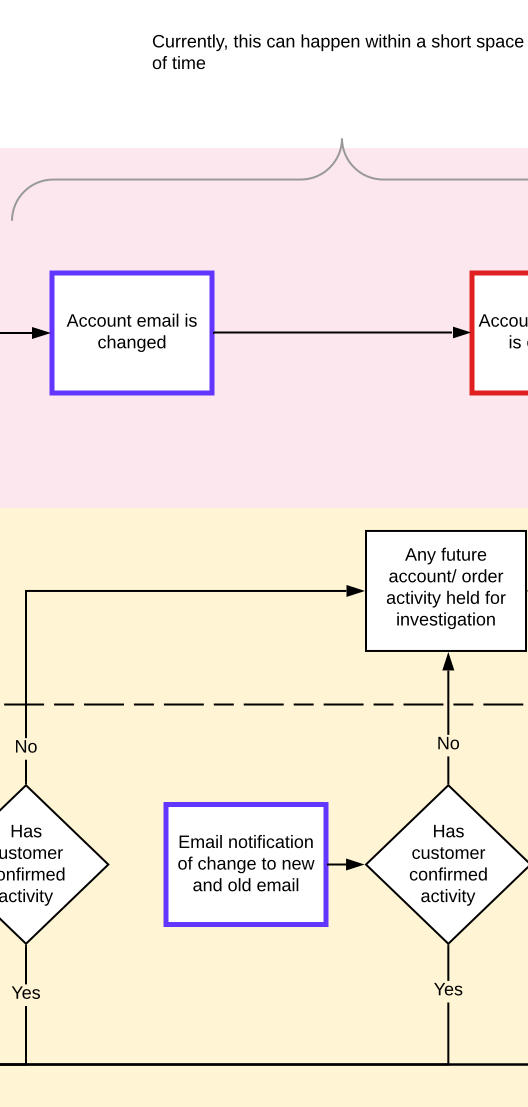
Should the unauthorised login be bypassed there would be a series of checks along the account take over route. The account would not be able to delete the current email until a new one had been entered. As soon as that is actioned an alert is sent to the default account to authorise.
The other option here is we start to gather back a back up email address within the prevention phase.
Either way, if the activity is not authorised and future orders would be automatically held until activity is authorised or the customer has contacted customer service.
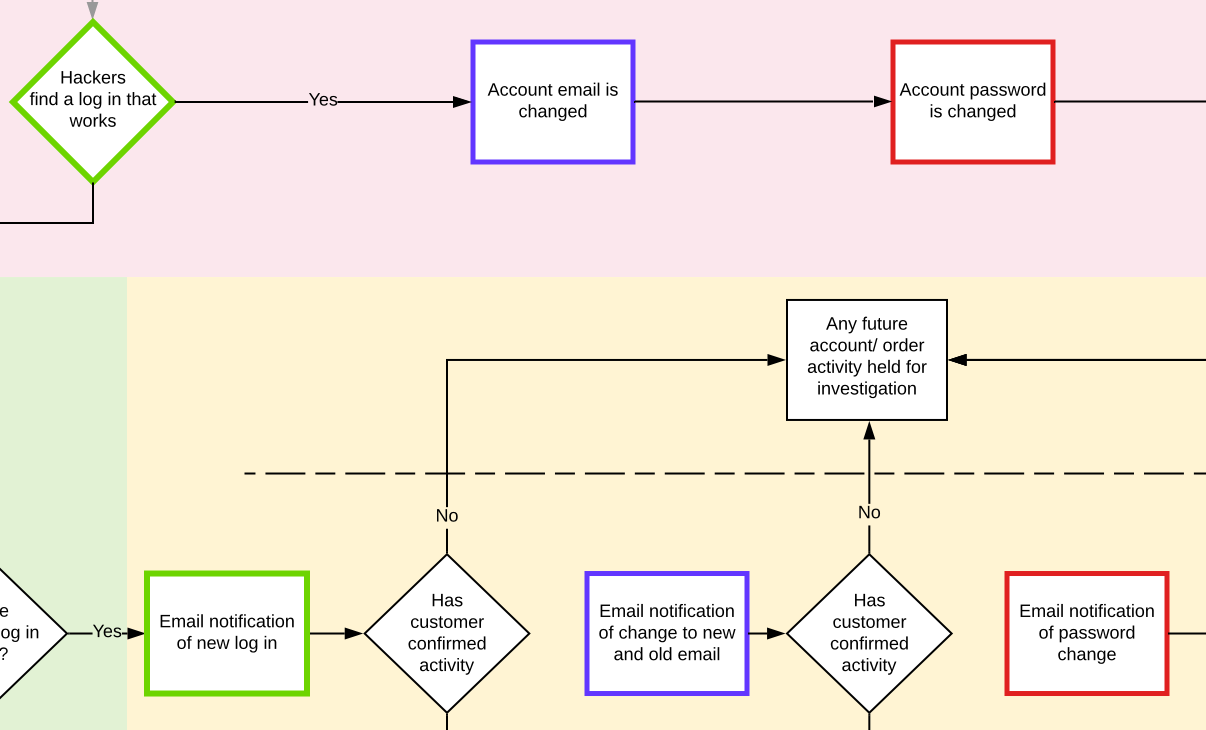
We now have another check point that could result in the account being suspended or held.
Should an email address have been added or deleted within the last 24 hours the account could be suspended for investigation or until the customer has acknowledged the account activity.
The person in the account and at the customer email will be made full aware of what is going through constant notification of account activity.
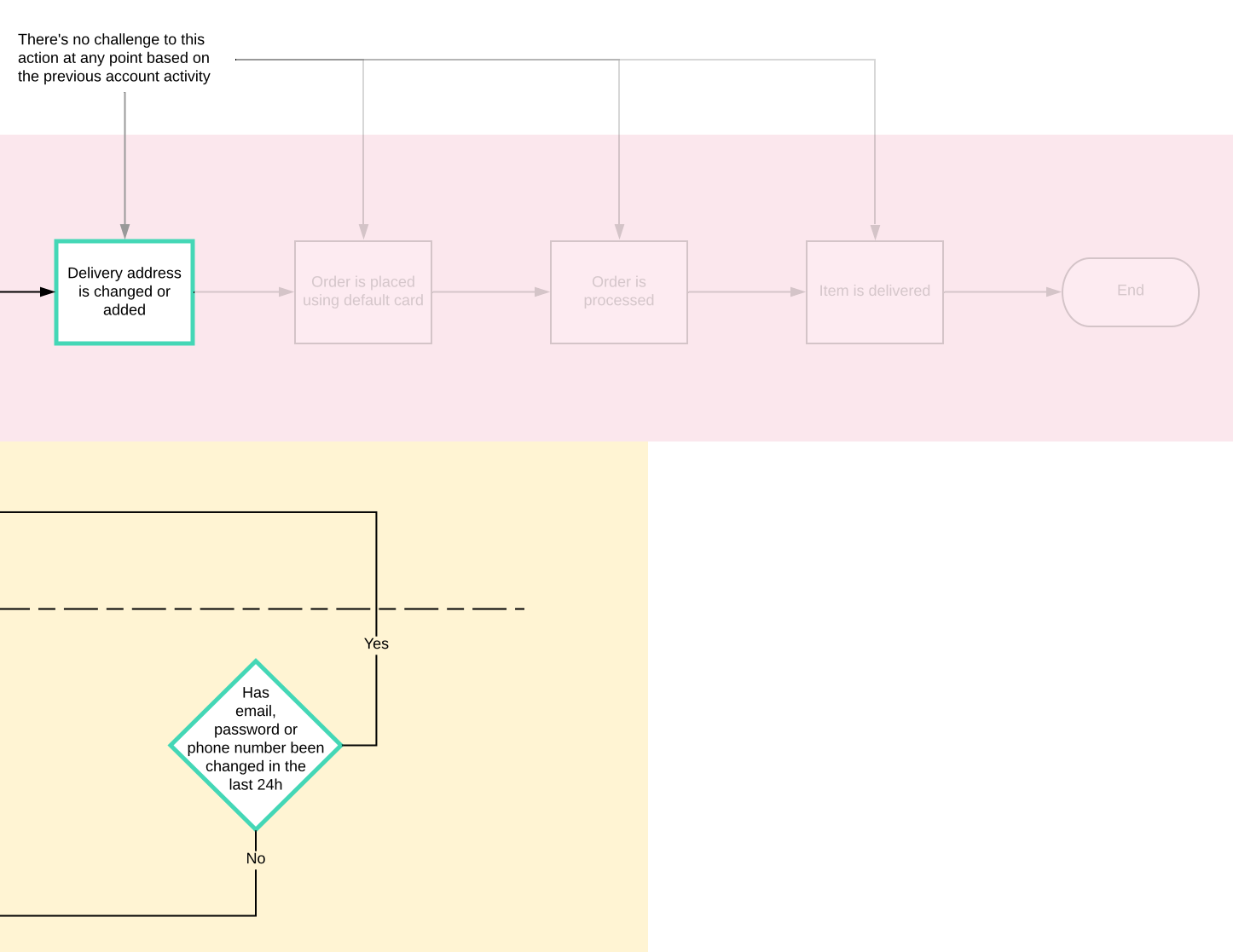
The final stage would be if the previous stages (Login, email or password change) haven't been acknowledged. If an order is being placed and the delivery address is changed there would be one final account hold. This one would be mainly linked to the login not being acknowledged.
Those faded out steps would never get actioned with the proposed flow so it would save the customers loosing access, trust and money while also making sure the business doesn't loose any more stock or money.
Final Thoughts
- MFA authorisation is secure - Only if people want it
- MFA isn't the best solution for our circumstances
- Research has shown uptake for MFA is slow
- Adding account activity notifications will help expose activity sooner and reduce the risk of loosing money.
- Suspicious activity account monitoring and holding could stop fraudulent orders being processed
- Forcing a complicated password will not fix the company loosing money